For various reasons many Apps need to detect if the phone has been “rooted” and in this article will see different techniques for this purpose. Since it is common to see this type of questions in development forums, I thought a post on the subject would be of interest to many readers.
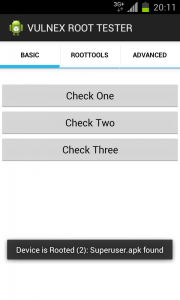
In this StackOverflow post we can find techniques commonly used in Apps for Rooted detection. The following code makes use of three methods for detecting Rooted: the first check for the string “test-keys”, which is a generic key for signing packages; the second method checks whether the Superuser.apk exist in disk, this App manages access to “su” command (administrator privileges) for other Apps; and finally the third method calls “su” directly and runs a root command.
/**
* @author Kevin Kowalewski
*
*/
public class Root {
private static String LOG_TAG = Root.class.getName();
public boolean isDeviceRooted() {
if (checkRootMethod1()){return true;}
if (checkRootMethod2()){return true;}
if (checkRootMethod3()){return true;}
return false;
}
public boolean checkRootMethod1(){
String buildTags = android.os.Build.TAGS;
if (buildTags != null && buildTags.contains("test-keys")) {
return true;
}
return false;
}
public boolean checkRootMethod2(){
try {
File file = new File("/system/app/Superuser.apk");
if (file.exists()) {
return true;
}
} catch (Exception e) { }
return false;
}
public boolean checkRootMethod3() {
if (new ExecShell().executeCommand(SHELL_CMD.check_su_binary) != null){
return true;
}else{
return false;
}
}
}
/**
* @author Kevin Kowalewski
*
*/
public class ExecShell {
private static String LOG_TAG = ExecShell.class.getName();
public static enum SHELL_CMD {
check_su_binary(new String[] {"/system/xbin/which","su"}),
;
String[] command;
SHELL_CMD(String[] command){
this.command = command;
}
}
public ArrayList executeCommand(SHELL_CMD shellCmd){
String line = null;
ArrayList fullResponse = new ArrayList();
Process localProcess = null;
try {
localProcess = Runtime.getRuntime().exec(shellCmd.command);
} catch (Exception e) {
return null;
//e.printStackTrace();
}
BufferedWriter out = new BufferedWriter(new OutputStreamWriter(localProcess.getOutputStream()));
BufferedReader in = new BufferedReader(new InputStreamReader(localProcess.getInputStream()));
try {
while ((line = in.readLine()) != null) {
Log.d(LOG_TAG, "--> Line received: " + line);
fullResponse.add(line);
}
} catch (Exception e) {
e.printStackTrace();
}
Log.d(LOG_TAG, "--> Full response was: " + fullResponse);
return fullResponse;
}
}
Apps on a not rooted phone cannot run either of these methods, since all Android Apps by default are in a sandbox (a system of process isolation) and with limited privileges.
The three methods described may be the most common and if we reverse engineering often we can find them in well-known Apps.
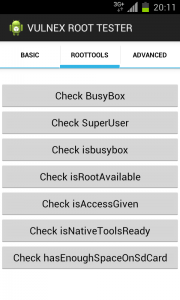
Other techniques include the use of the fantastic RootTools library that facilitates the development of Apps that need root offering various tools. Many Apps use this library.
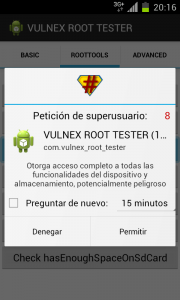
Library features include check if it exists or offers to install BusyBox (program that combines many Unix utilities in a small single executable), check if it exists or offers to install SuperUser, verify that App has root access, native tools or enough space on the SD Card.
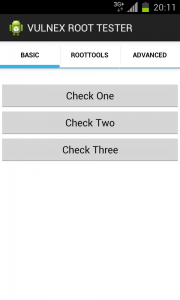
As an exercise to test these root detection techniques, I have written the VULNEX ROOT TESTER that combines different techniques from the basic here presented to some more sophisticated that we will cover in another post. Find below some screenshots of the tool.
No doubt the ability to detect Rooted may be necessary for certain Apps that require a high level of security, but also for many legitimate Apps, such as various security Apps, that require root to function properly or take maximum advantage of the Android platform.
We have to bear in mind that to develop a secure App it is not enough to detect Rooted, but we should think about making a threat modeling of the potentials risks to our App, secure development practices (for example OWASP Mobile) and apply code obfuscation techniques among many other security measures, in order to mitigate vulnerabilities and hinder reverse engineering. My recommendation is that if you are not familiar with these concepts you should talk to some application security professional and get help.
What techniques is your App using to detect Rooted, if any?
— Simon Roses Femerling