In recent years all “cyber” is fashionable, and intelligence applied to the cyber world could not be less! The concept of intelligence has an offensive meaning due to the use by intelligence and military agencies, but now too many security vendors position their products as intelligence solutions able to identify potential threats.
With the use of these security products many private organizations “believe” that they are getting intelligence but their vision is very limited:
- The intelligence is obtained by the quantity and quality of their sources (many organizations don’t know nor their sources of information).
- The human analysis factor is vital (is not about installing a product and expect a detailed report, like everything is automated.)
- The focus is just outside threats (Internet) as internal threats do not exist.
It is funny or sad (depending on how you look at it) when many organizations and security vendors talk about their ability to monitor and analyze systems logs, antivirus, firewall, IDS, Honeypots, etc. to provide intelligence and then they don’t know the number of computers, users or software installed in the organization. Intelligence applied only to the outside is insufficient when internal threats are unknown.
In VULNEX (disclaimer: cybersecurity startup founded by my) we gave it some thought and developed some solutions that help in this regard, for example BinSecSweeper: a tool to analyze Windows, Linux and MacOS binaries. We can take an operating system and analyze all the binaries to determine their security posture (for example scanning all the 7000aprox binaries in Kali Linux in 30 minutes 😉 or determine if software is using obsolete libraries among other things.)
Software today is not written but composed: programmers use different libraries and commercial or open source code to compose their product in the shortest time possible and push it to market. Organizations use all kind of software without knowing whether it is safe or what is composed of, huge mistake!
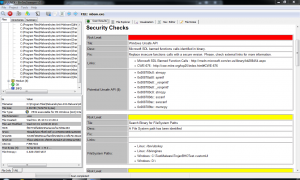
Fig. 1 – Scanning software with BinSecSweeper, a peak under the hood
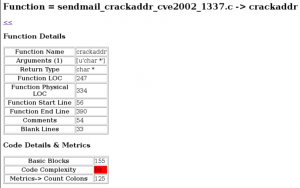
Another need we got in VULNEX is to obtain intelligence from source when doing code audits. These audits are complex, long and usually limited in time so it is necessary to obtain valuable information to focus on the work. In this sense we have developed Tintorera, a plugin for GCC that, while we compile a project in C, performs an analysis that helps us understand the code without having read the source itself. At this point we are not looking for vulnerabilities, but we do want to understand the relationship between functions, code metrics, complexity, and other parameters that help us be more effective to scrutinize the code and find vulnerabilities. Intelligence applied to source code!
If you believe that your organization is doing cyber intelligence, think again and really determine your analysis capabilities and what is your vision that surely are not as good as you think…
No doubt much remains to be done in the Cyber intelligence at both internal and external sources to obtain a real and global view of threats.
Does your organization have a cyber intelligence program?
— Simon Roses Femerling @simonroses