Disclaimer: Everything described here is pure imagination and any resemblance to reality is coincidental. The author is not responsible for the consequences of any action taken based on the information provided in the article.
The Davos Forum organized by the World Economic Forum (WEF) is the economic event of the year that brings together thousands of people from all over the world, from politicians to well-known businessmen, in the town of Davos, Switzerland.
Thousands of people gather in Davos from political personalities and businesses to support, administrative and security personnel. We define as primary objectives politicians (presidents, prime ministers, and the like) and relevant businessmen (presidents and CEOs); and secondary objectives such as support personnel, who, by compromising their security, allow the surveillance or exploitation of primary objectives.
During the Davos Forum, the security of the people is protected between police, military and security personnel, different security rings, access control, special permits for vehicles, anti-drone systems, etc. are established.
For this exercise we will assume that a Nation-State deploys a unit of cyber operatives and field agents in Davos to carry out offensive operations such as spying, installing implants or other subversive activities.
This operation is divided into different phases: preparations before the forum, actions during the forum and post-forum actions. The post-forum actions would be related to persistence, command and control of the objectives and exfiltration of information that we are not going to comment on in this post. Therefore, we are going to focus on the phases before and during the forum.
Preparations before the forum
Preparations prior to the offensive campaign during Davos would include at least the following points:
- Selection of objectives: We have previously defined between primary and secondary objectives, at this point we are going to focus on the primary ones only. Politicians and businessmen usually carry high-end smartphones, mainly the latest model iPhone or an older model. Cyber operatives will use OSINT techniques to search for images or videos that can be used to identify the smartphone model. They can also search for public documentation on the acquisition of devices, such as the Spanish Congress did in 2023 with the purchase of iPhones 13 for all deputies.
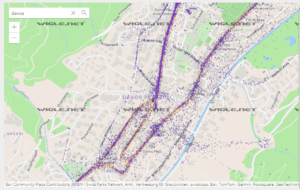
- Identification of RF devices: By using portals such as Wigle and similar, cyber operatives can obtain names of WIFI access points, Bluetooth devices and mobile phone towers in the geographical area. This information is useful for planning RF attacks, also known as proximity attacks, which are generally unknown and undervalued by organizations.
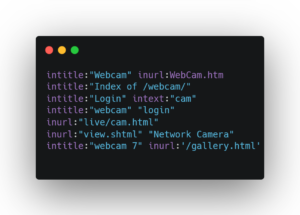
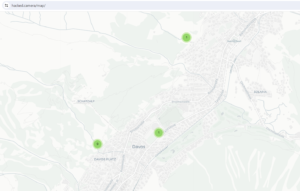
- Identification of CCTV devices: Using portals such as Shodan and similar, cyber operatives can search for cameras in Davos to compromise their security and use them for surveillance and monitoring tasks. In the following images we see some Google Dorks
, also known as Google Hacking, to search for cameras on the Internet and on the Hacked.camara
web portal we can find hacked cameras in the Davos area. - Development and/or purchase of Exploits: Exploits are the cyber weapons that cyber operatives will use to compromise the targets’ devices. Zero-day vulnerability exploits (vulnerabilities not known to the manufacturers and unpatched) will surely be necessary for systems such as Windows, MacOS, iPhone (iOS) and Android. These types of exploits are expensive (from hundreds of thousands to millions of euros) and nowadays it is usually necessary to have several to be able to compromise the security of a device and be able to bypass all security levels. To get an idea of the cost and complexity, I recommend reading about Operation Triangulation, a recent campaign against a well-known cybersecurity manufacturer in which some of its iPhones were compromised using several zero-day exploits.
- Development of Implants: Once access is achieved, it is necessary to deploy implants in the compromised systems to control them and exfiltrate information. As with exploits, cyber operatives must have implants for the different Windows, MacOS, iPhone (iOS) and Android systems. These implants can be developed or purchased on the market and the reality is that many times they do not have to be anything sophisticated to achieve good results. A real example is the use of Pegasus spyware to spy on politicians in Europe.
- Equipment: Cyber operatives will have to carry all the software and hardware equipment they may need such as: laptops, WIFI access points, “Lock Picking” tools, antennas, drones, WIFI and Bluetooth adapters, offensive hardware (see my article about it to get an idea), cameras, microphones, and a long etcetera.
Image: Davos devices seem in Wigle
Image: Google Dorks
Image: Hacked CCTV at Davos
Good preparation is crucial for successful cyber-attacks during Davos.
During the forum
During the days of the Davos Forum, cyber operatives can execute a wide range of cyber-attacks to achieve their objectives. Next, we will look at possible attacks and with real examples when possible.
- Deployment of fake phone towers to intercept traffic and/or send exploits to mobile phones. These devices are also known as IMSI-catcher. Cyber operatives could deploy these devices before the event, but for their operational security (OPSEC) they decide to use this attack during the event. A real case was the detection of fake cell towers around the US White House.
- Social engineering: This old and well-known attack still works, although it has been modernized with the use of emails, SMS, and instant messaging (IM). Without a doubt, female operatives in Davos could gain a wealth of valuable information or access to targets’ electronic devices that would allow them to install an implant. A real case is the use of female Russian spies to infiltrate NATO.
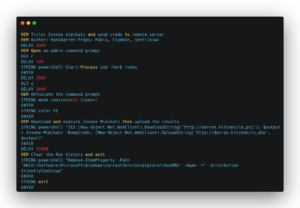
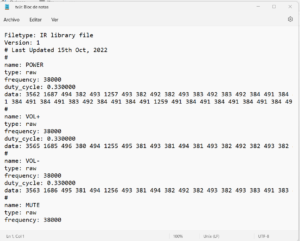
- USB Drop attack: consists of leaving USBs lying on the floor or in some visible place such as a table and containing malware. When they are found and someone inserts them into a computer to see what’s inside, exploiting human curiosity, and perhaps returning it to its owner, it is infected by malware and now the cyber operatives control the device. A well-known and simple offensive programming language is DuckyScript, supported by a multitude of offensive devices, and which allows you to create scripts with payloads for Windows, MacOS, Linux, iPhone (iOS) and Android. I recommend the payloads repository available to understand its capabilities. The following image is a well-known script to steal passwords on Windows in a matter of seconds using a USB Rubber Ducky, a known offensive device.
- WIFI attacks: another well-known attack is to attack WIFI access points or create malicious WIFI points. There are many offensive devices such as the popular WIFI Pineapple although a laptop, a Wi-Fi card and a good antenna are sufficient. A real case is the use of drones equipped with offensive devices such as the WIFI Pineapple that allow them to land on a rooftop to launch WIFI attacks, as happened in the US against a financial company. Cyber operatives can also walk around the Davos area with covert offensive devices that allow them to break WIFI networks automatically or capture the “handshakes” of WIFI connections, to break them and gain access. All access points and WIFI clients are susceptible to different attacks.
- Bluetooth attacks: Bluetooth attacks are on the rise, although they require proximity, they can be devastating since in some cases they allow control of the victim device, and best of all, they are undervalued by most organizations. There are many attacks available but two attacks that cyber operatives could use to compromise the security of devices is BlueBorne and a new attack on the Bluetooth protocol has recently been published affecting Android, MacOS, iPhone (iOS) and Linux that connects a fake keyboard without user approval. Today billions of devices remain vulnerable to these attacks.
Image: DuckyScript
Despite the high security measures during the Davos Forum, it is undoubtedly a very interesting objective for a Nation-State with so many politicians and businessmen concentrated in the same place.
As we have seen throughout the article, the possibility of offensive operations in Davos is a reality and all necessary physical and digital security measures must be taken.
Leave me your comment on the article, please, and what topics would you like me to go into more depth?
— See you on @simonroses